We, DBAs, have a tendency to over think everything. I don’t know if the trait to over think is just found in DBAs or if we see it in other technical positions, too.
I believe it corresponds to some of why we become loyal to one technology or platform. We become accustomed to how something works and it’s difficult for us to let go of that knowledge and branch out into something new. We also hate asking questions- we should just be able to figure it out, which is why we love blog posts and simple documentation. Just give us the facts and leave us alone to do our job.
Take the cloud- Many DBAs were quite hesitant to embrace it. There was a fear of security issues, challenges with network and more than anything, a learning curve. As common, hindsight is always 20/20. Once you start working in the cloud, you often realize that its much easier than you first thought it would be and your frustration is your worst enemy.
So today we’re going to go over some basic skills the DBA requires to manage a cloud environment, using Amazon, (AWS) as our example and the small changes required to do what we once did on-premise.
In Amazon, we’re going to be working on EC2, also referred to as the Elastic Compute Cloud.
Understanding Locations, Regions and Zones
EC2 is built out into regions and zones. Knowing what region you’re working in is important, as it allows you to “silo” the work you’re doing and in some ways, isn’t much different than a data center. Inside of each of these regions, are availability zones, which isolates services and features even more, allowing definitive security at a precise level, with resources shared only when you deem it should.
Just as privileges granted inside a database can both be a blessing and a curse, locations and regions can cause challenges if you don’t pay attention to the location settings when you’re building out an environment.
Amazon provides a number of links with detailed information on this topic, but here’s the tips I think are important for a DBA to know:
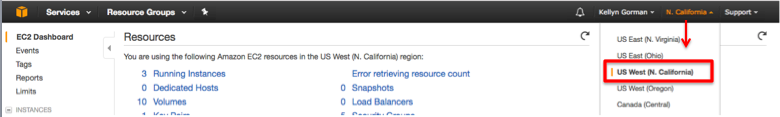
- Before setting anything up that is part of a complete solution requiring multiple setup page configurations, ALWAYS check the region in the upper right corner. I was surprised when it would change from page to page or after a login-
2. If you think you may have set something up in the wrong region, the dashboard can tell you what is deployed to what region under the resources section:
Understanding Security Keys
Public key cryptography makes the EC2 world go round. Without this valuable 2048-bit SSH-2 RSA key encryption, you can’t communicate or log into your EC2 host securely. Key pairs, a combination of a private and public key should be part of your setup for your cloud environment.
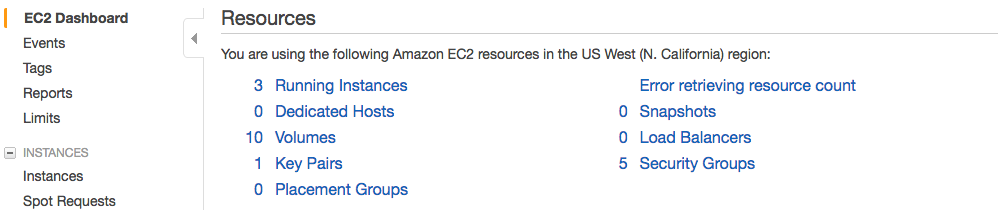
Using EC2’s mechanism to create these is easy to do and eases management. Its not the only way, but it does simplify and as you can see above in the resource information from the dashboard, it also offers you a one-stop shop for everything you need.
When you create one in the Amazon cloud, the private key downloads automatically to the workstation you’re using and it’s important that you keep track of it, as there’s no way to recreate the private key that will be required to connect to the EC2 host.
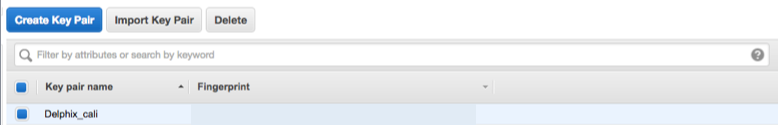
Your key pair is easy to create by first accessing your EC2 dashboard and then scroll down on the left side and click on “Key Pairs”. From this console, you’ll have the opportunity to create, import a pre-existing key or manage the ones already in EC2:
Before creating, always verify your region you’re working in, as we discussed in the previous section and if you’re experiencing issue with your key, verify typographical errors and if the location of the private file matches the name listed for identification.
If more than one group is managing the EC2 environment, carefully consider before deleting a key pair. I’ve experienced the pain caused by a key removal that created a production outage. Creation of a new key pair is simpler to manage than implementation of a new key pair across application and system tiers after the removal of one that was necessary.
Understanding Roles and Security
Security Groups are silo’d for a clear reason and no where is this more apparent than in the cloud. To ensure that the cloud is secure, setting clear and defined boundaries of accessibility to roles and groups is important to keep infiltrators out of environments they have no business accessing.
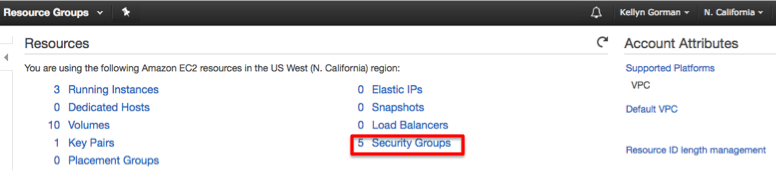
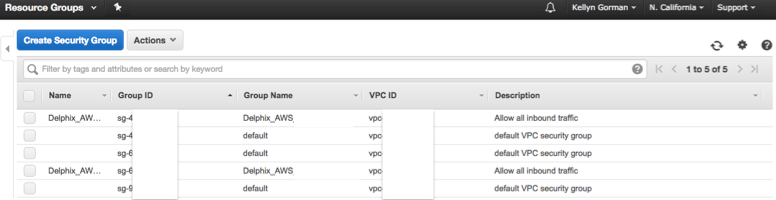
As we discussed in Key Pairs, our Security Groups are also listed by region under resources so we know they exist at a high level. If we click on the Security Groups link under Resources in the EC2 Dashboard, we’ll go from seeing 5 security group members:
To viewing the list of security groups:
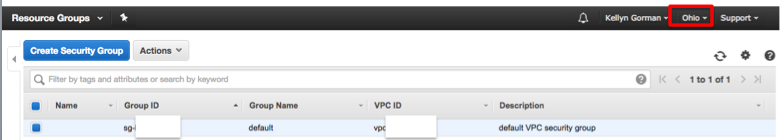
If you need to prove that these are for N. California, (i.e. US-West-1) region, click on the region up in the top right corner and change to a different region. For our example, I switched to Ohio, (us-east-2) and the previous security groups aren’t listed and just the default security group for Ohio region is displayed:
Security groups should be treated in the cloud the same way we treat privileges inside a database- granting the least privileges required is best practice.
Understanding How to SSH to a Host
You’re a DBA, which means you’re most likely most comfortable at the command line. Logging in via SSH on a box is as natural as walking and everything we’ve gone through so far was to prepare you for this next step.
Your favorite command line tool, no matter if it’s Putty or Terminal, if you’re set up everything in the previous sections correctly, then you’re ready to log into the host, aka instance.
- Ensure your downloaded private key is saved in an easily accessible spot for you to use to log in or that you know the username/password, (keys just make this easier…)
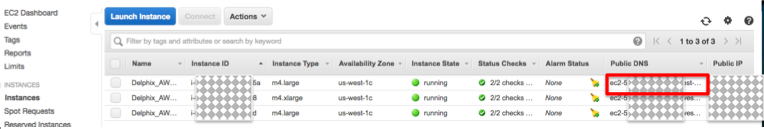
- Gather the information about “instances” by clicking on the EC2 dashboard, then click on Instances.
- The Public DNS and the Public IP is displayed and note the region, too:
You can use this information to then ssh into the host:
ssh -i "<keypair_name>.pem" <osuser>@<public dns or ip address>.<region>.compute.amazonaws.com
Once logged in as the OS user, you can SU over to the application or database user and proceed as you would on any other host.
If you attempt to log into a region with a key pair from another region, it state that the key pair can’t be found, so another aspect showing the importance of regions.
Understanding How to SCP a File
This is the last area I’ll cover today, (I know, a few of you are saying, “good, I’ve already got too much in my head to keep straight, Kellyn…)
With just about any Cloud offering, you can bring your own license. Although there are a ton of images, (AMIs in AWS, VHDs in Azure, etc.) pre-built, you may need to use a bare metal OS image and load your own software or as most DBAs, bring over patches to maintain the database you have running out there. Just because you’re in the cloud doesn’t mean you don’t have a job to do.
Change over to the directory that contains the file that you need to copy and then run the following:
scp -i <keypair>.pem <file name to be transferred> <osuser>@<public dns or ip address>.<region>.compute.amazonaws.com:/<direction you wish to place the file in>/.
If you try to use a key pair from one region to log into a SCP to a host, (instance) in another region, you won’t receive an error, but it will act like you skipped the “-i” and the key pair and you’ll be prompted for the password for the user:
<> password: pxxxxxxxxxxxx_11xxxx_Linux-x86-64.zip 100% 20MB 72.9KB/s 04:36
This is a good start to getting started as a DBA on the cloud and not over-thinking. I’ll be posting more in the upcoming weeks that will not only assist those already in the cloud, but those wanting to find a way to invest more into their own cloud education!


You’re opening hit me like a ton of bricks! I can totally relate. Thanks for the great article!!
Thank you- promise to have more soon! 🙂
Good one.
Great article again K
Thank you!