Lately I’ve been having more discussions on securing the EM12c environment. All of IT has a tendency to treat the Enterprise Manager as a afterthought in both hardware allocation, as well as security best practices. No one is sure of exactly why this is- they all have their theories, but we do know it happens often.
Today we are going to go over some of the auditing options within EM12c. Basic auditing is turned on by default in the environment, but only covers basics processes. There are over 150 auditing options and extensive information can be collected, retained within the repository, as well as turned into an externalized service to reside as log files on the OS file system. These options include login/logout information, updates, OMS password changes and EM key copy and removals from the repository.
Basic auditing information can be gained through the console via the Setup, Security, Auditing Data menu option, but the auditing configuration, additional features, updates and externalized service setup, must be performed through the Enterprise Manager command line interface, (EM CLI).
If you haven’t used the EM CLI before, please refer to my blog post on Beginning with the Command Line Interface, otherwise log in a user with appropriate rights to run the EM CLI and connect to the repository.
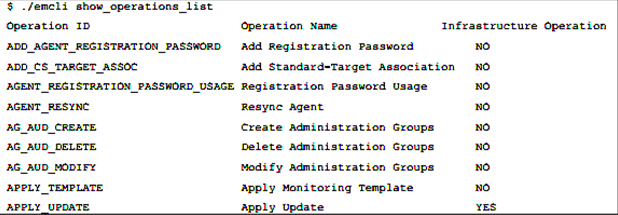
First, let’s inspect the current operations list and what will impact the infrastructure if executed:
Note that the last option, APPLY_UPDATE, is to update the repository and yes, it will impact the infrastructure by doing so.
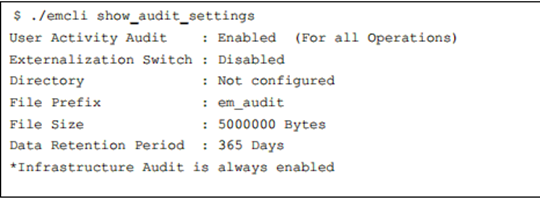
Next, let’s look at the current settings. As I stated earlier, auditing is turned on by default, but the next options are disabled for the externalized service, so it is marked as disabled.
The defaults for the externalized service, outside of the directory, (configured in the DBA_DIRECTORIES and read/write privileges granted to SYSMAN) are pre-configured with default information.
- File prefix is the prefix used for all audit log files so that they are easily identified in the directory.
- File size is default to 50M
- Retention is default to 365 days. Keep this in mind before enabling, as this could be impacting to disk space if you OS directory has limited space.
Notice that there is also a note informing you that Infrastructure Audit is always on, (go inspect the access.log and you will see information that can be sync’d up with the emctl.log and others to create a solid picture that this feature can create for you.)
Enabling/Disabling Features
To enable or disable audit features, the following syntax is used:
>emcli update_audit_settings -audit_switch="ENABLE/DISABLE" -
operations_to_enable="<insert operation name here or just say ALL>" -
operations_to_disable="<insert operation name here or just say ALL>"
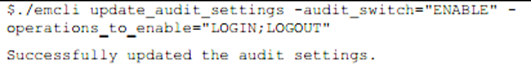
To demonstrate this, we’ll enable auditing for logins and logouts:
The response letting us know if the change was successful in the auditing configuration completes the task and we can move on to other tasks.
Next, we’ll configure the externalized service for auditing. This is an excellent choice and should be considered for all EM12c environments. Even with high availability options, the idea of keeping a minimum of 7-31 days of auditing information regarding the EM12c environment, especially considering the access and power of the EM12c, is a good idea.
The syntax for the configuration for the externalized auditing service is:
>emcli update_audit_settings -file_prefix=<file_prefix> -
directory_name=<directory_name> -file_size = <file size> -data_retention_period=<period in days>
And in our example, we will update the service to file sizes of 25M each, with a prefix of “em12c_audit” and retain 31 days of audit files that our OS file system can easily handle.
>emcli update_audit_settings -externalization_switch=ENABLE -file_prefix=em12c_audit -directory=AUD_DMP -file_size=25000000 -data_retention_period=31
After executing this statement, the audit files will automatically start generating to the directory, (make sure you HAVE created a DBA Directory to hold this data first!) and we can then view logs as needed to inspect what activity is occurring in the EM12c environment.
This is a solid best practice to ensure you are offering one more line of protection to the database and software that is essential to you, your business and your environment.