I’ve been hesitant to post too much on my blog until since the hack, as there were some residual issues after the restoration of the site that took a bit to correct. I’m finally feeling confident enough to start posting on everything I’m doing currently working with Azure and the education customers for Microsoft.

One of the powerful tools I’ve been taking advantage of is the Azure Cloud Shell. This cloud tool has the offering option of setting to PowerShell or Bash and I think you know which I chose.
Although everything I do will require a PowerShell version in a later phase, the bash skills are strong in this one and it only makes sense that I would take on new technology in the language that I already know to remove an extra layer of challenges.
As you work with Azure and Microsoft products, (or with any Cloud platform) you’ll be required to build firewall rules to access from your local workstation or from any location, to the cloud environment. Microsoft has done an impressive job as new releases and updates come out, to build an automated step to offer a firewall rule creation from most products, removing the manual step requirement.
With my use of scripting and Azure Cloud Shell, I’m automating and building my environment, including SQL Database resources and then have a requirement to access and build the logical objects. This means that I need a firewall rule build for the Azure Cloud Shell I’m working from. The IP for this cloud shell is unique to the session I’m running at that moment.
The requirement to add this enhancement to my script is:
- Capture and read the IP Address for the Azure Cloud shell session.
- Populate the IP Address to a Firewall rule
- Log into the new SQL Server database that was created as part of the bash script and then execute SQL scripts.
Capture the IP Address from the Azure Cloud Shell
I chose to use a curl command to pull the correct IP6v address for the Azure Cloud Shell. There are a number of sites it can hit that will return the address to pass to the firewall creation script.
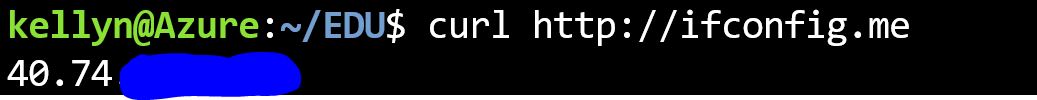
I used ifconfig.me, but there’s https://canihazip.com and a slew of others if you do a websearch. To populate the values in the script, it sets the following:
echo "getting IP Address for Azure Cloud Shell for firewall rule"export myip=$(curl http://ifconfig.me)export startip=$myipexport endip=$myip
The creation command for a firewall requires a starting IP and ending IP, so both are going to receive the single IP address. This is an Azure resource creation command:
az sql server firewall-rule create \
--resource-group $groupname \
--server $servername \
-n AllowYourIp \
--start-ip-address $startip \
--end-ip-address $endipWhen it executes inside the script, the following will be displayed in the output:
"endIpAddress": "40.74.xxx.xxx",
"id": "/subscriptions/73aaxxxxx-xxxx-xxxx-xxx/resourceGroups/EDU_Group/providers/Microsoft.Sql/servers/hiedxxxxxsql1/firewallRules/AllowYourIp",
"kind": "v12.0",
"location": "East US",
"name": "AllowYourIp",
"resourceGroup": "xxx_Group",
"startIpAddress": "40.74.xxx.xxx",
"type": "Microsoft.Sql/servers/firewallRules"
The script is able to use the IP Address from the curl command to create the firewall rule and then the new rule is used by the Azure Cloud Shell to access the SQL Server it’s been created for.
I can now execute my scripts against my databases:
sqlcmd -U $adminlogin -S ${servername}.windows.net -P "$password" -d HiEd_DW -i "./edu_hied_DW.sql;"
That’s all there is to creating a dynamic firewall rule and using it from any console product, not just the Azure Cloud Shell.
Enjoy!





One comment on “Dynamic Firewall Creation for Azure Cloud Shell”
Comments are closed.